Application Security Gap Assessment
As the digital landscape continues to evolve, the importance of robust security measures to safeguard sensitive data and critical assets cannot be overstated.
Audit my Application Security
Identify any potential vulnerabilities or weaknesses
Here are some compelling reasons why investing in an Application Security Assessment is imperative:
Risk Mitigation
Identifying and addressing security gaps proactively helps mitigate the risk of data breaches, financial losses, and reputational damage to your organization.
Compliance Requirements
With increasingly stringent regulatory requirements such as GDPR, HIPAA, and PCI-DSS, ensuring the security of your applications is essential for maintaining compliance and avoiding hefty fines.
Protecting Customer Trust
Strengthening your application security demonstrates your commitment to protecting the privacy and trust of your customers, thereby enhancing your brand reputation.
Our Process
Our comprehensive Application Security Assessment aims to provide your organization with invaluable insights into the current state of security surrounding your applications. By conducting this assessment, we seek to identify any potential vulnerabilities or weaknesses that malicious actors could exploit, thereby jeopardizing the integrity and confidentiality of your data.
Determine Current State
This step involves assessing and documenting the current state of the organization, system, process, or performance. It may involve collecting data, conducting interviews, surveys, or using other assessment methods to gather information about the existing situation.
Define Desired Future State
Once the current state is understood, the next step is to define the desired future state or the goals that the organization wants to achieve. This involves identifying the ideal outcomes, objectives, or performance levels that the organization aims to reach.
Identify Gaps
With the current state and desired future state established, the next step is to compare the two and identify the gaps or differences between them. This involves analyzing the discrepancies between where the organization currently stands and where it wants to be, identifying areas of improvement, and understanding the root causes of the gaps.
Develop Action Plan
Based on the identified gaps, the final step involves developing an action plan or strategy to bridge the gaps and move the organization from its current state to the desired future state. This action plan may include specific initiatives, projects, or changes that need to be implemented, along with timelines, responsibilities, and resources required for execution.
The deliverables
Below are some sample deliverables our team offers to our clients, tailored according to the selected approach:

Prioritized Roadmap
A prioritized roadmap neatly showcases the major outcomes and deliverables that Takumi Cloud will prepare for a client. Based on the findings from an application security assessment or gap analysis, tasks for remediation are prioritized off of their impact and severity in order to close the most important gaps first. Clients and relevant teams receive a strategic plan that communicates upcoming changes effectively to ensure visibility from start to finish.
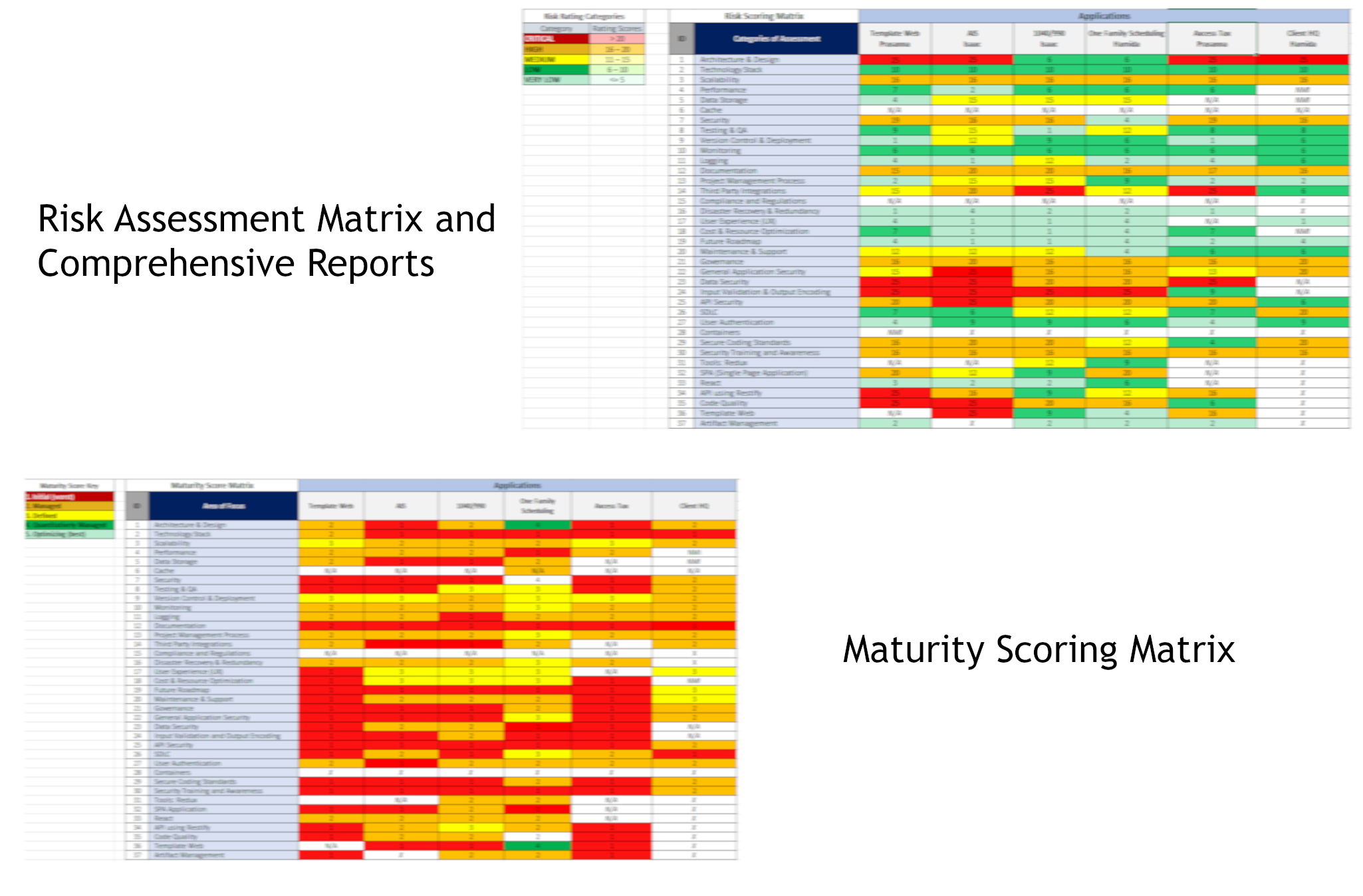
AppSec Assessment
An application security assessment is a comprehensive evaluation of the security measures implemented within a software application. This assessment involves identifying and analyzing potential vulnerabilities, threats, and risks that could compromise the confidentiality, integrity, and availability of the application and its data. The results can be showcased in a risk matrix to look into which security areas an application needs attention.
Reducing Risk and Ensuring Compliance
Ensuring your success remains our utmost priority. That's why it is crucial for us to offer our expertise in these intricate matters. However, our commitment to supporting you extends beyond this:
Total transparency on standard requirements
High-level on-prem, cloud and cybersecurity expertise to deliver quality audit's rapidly
Compliance done right! Implementation that does not take away from existing personel.
Rapid deployment as in any industry





